Creating an Incident Action
After creating a Job, the user can configure Action - the action that the system will perform if the search query in the Job is triggered. For more information, see here.
Example.
Creating an incident using Job Scheduler. For more information about parameters, see here.
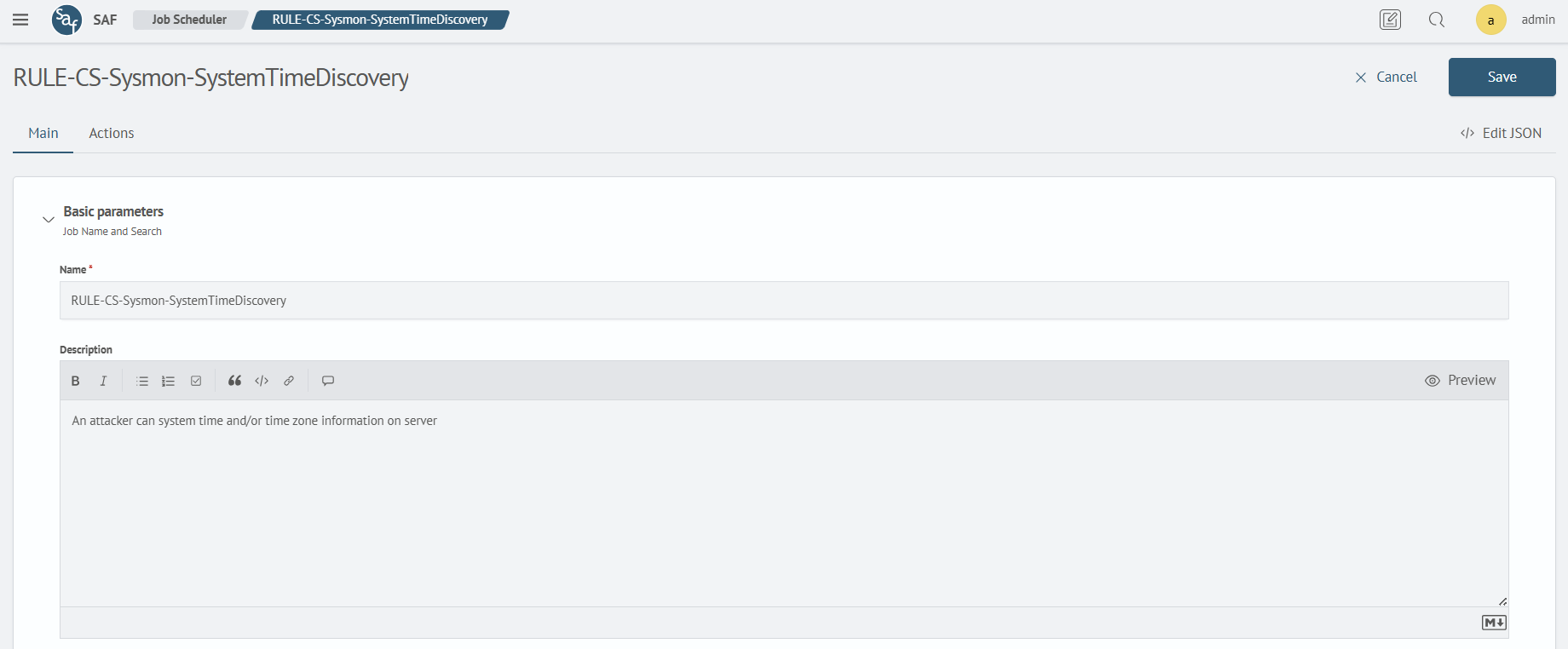
Enter the Name and Description of new job.
- Name -
RULE-CS-Sysmon- SystemTimeDiscovery - Description - An adversary may gather the system time and/or time zone from a local or remote system
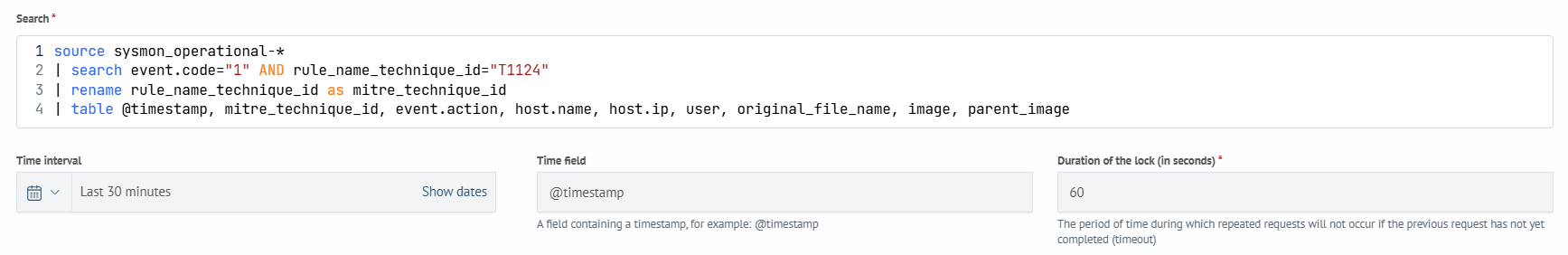
Enter the Search, Time interval, Frequency of execution, Suppression of execution, Global Params.
Search:
source sysmon_operational-*
| search event.code="1" AND rule_name_technique_id="T1124"
| rename rule_name_technique_id as mitre_technique_id
| table @timestamp, mitre_technique_id, event.action, host.name, host.ip, user, original_file_name, image, parent_image, command_line, parent_command_line, process_id, parent_process_id, process_guid, parent_process_guid
Time interval:
- Time interval - Last 30 minut
- Time interval -
@timestamp - Duration of the lock (in seconds) - 60
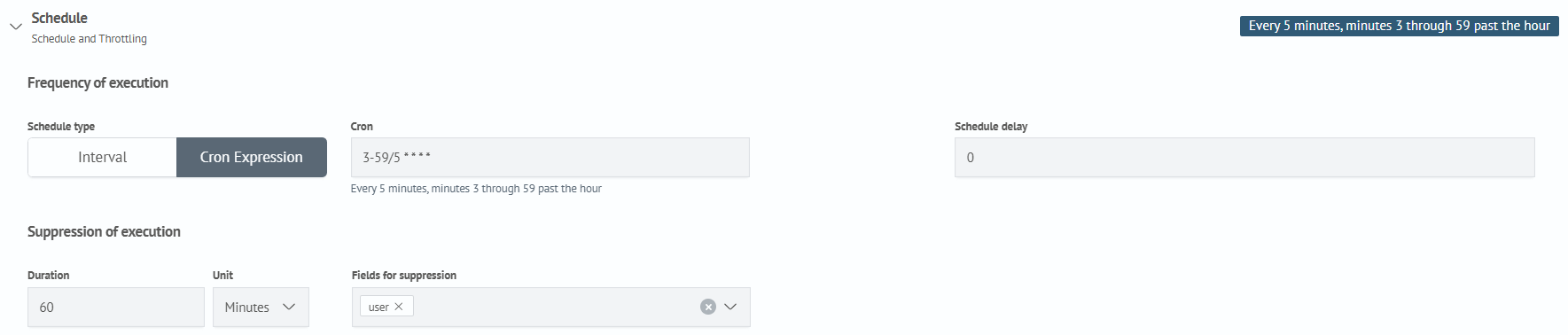
Frequency of execution:
- Schedule type - Cron Expression
- Cron - 3-59/5 * * * *
- Schedule delay - 0
Suppression of execution:
- Duration - 60 minut
- Fields for suppression -
user
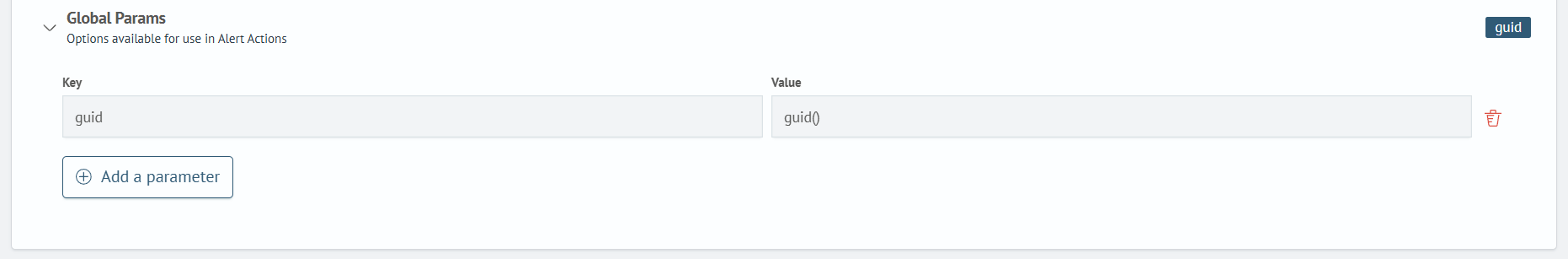
Global Params:
- Key -
guid - Value -
guid()
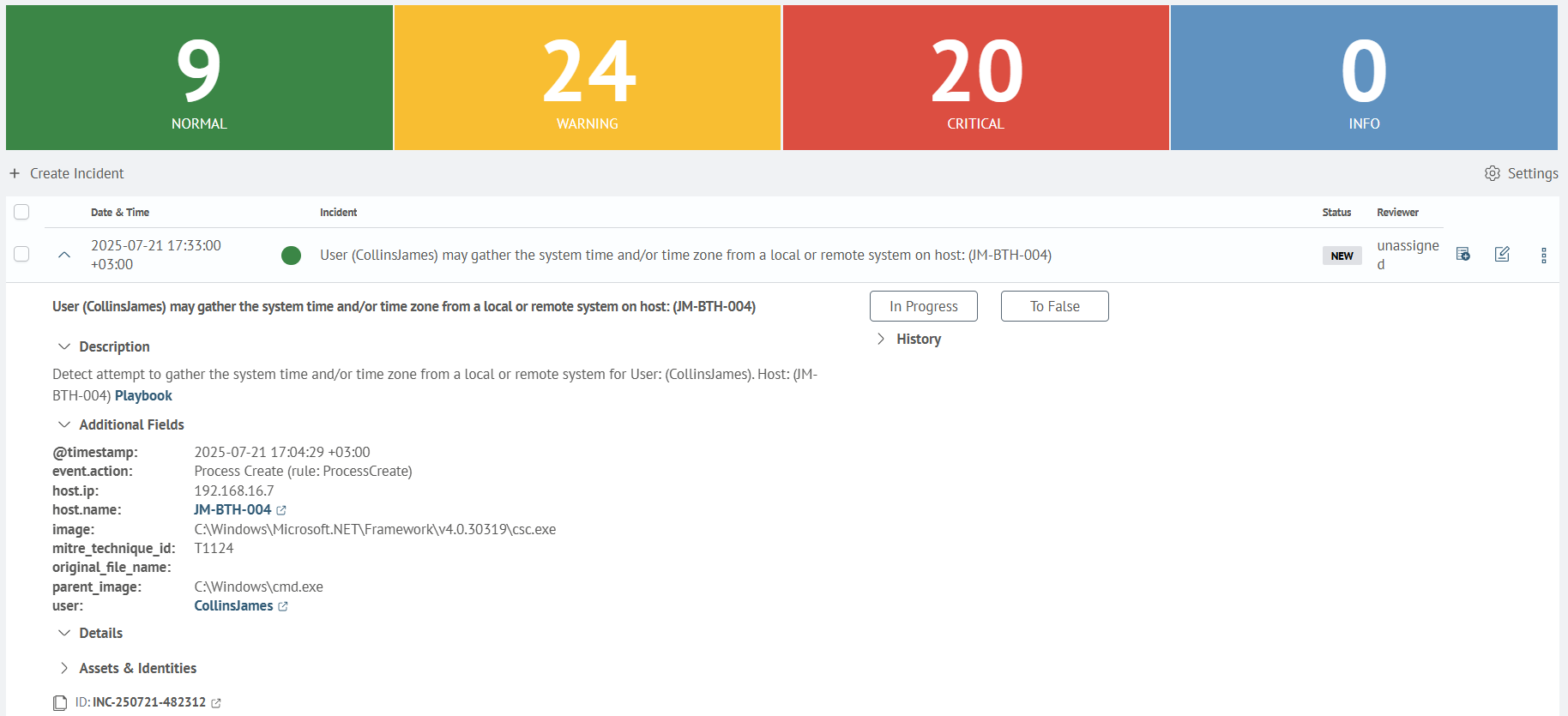
To log incidents using a search task, you need to add the Create Incident action in the Active Actions tab. Details on how to configure it are provided on the following page Incident Action.
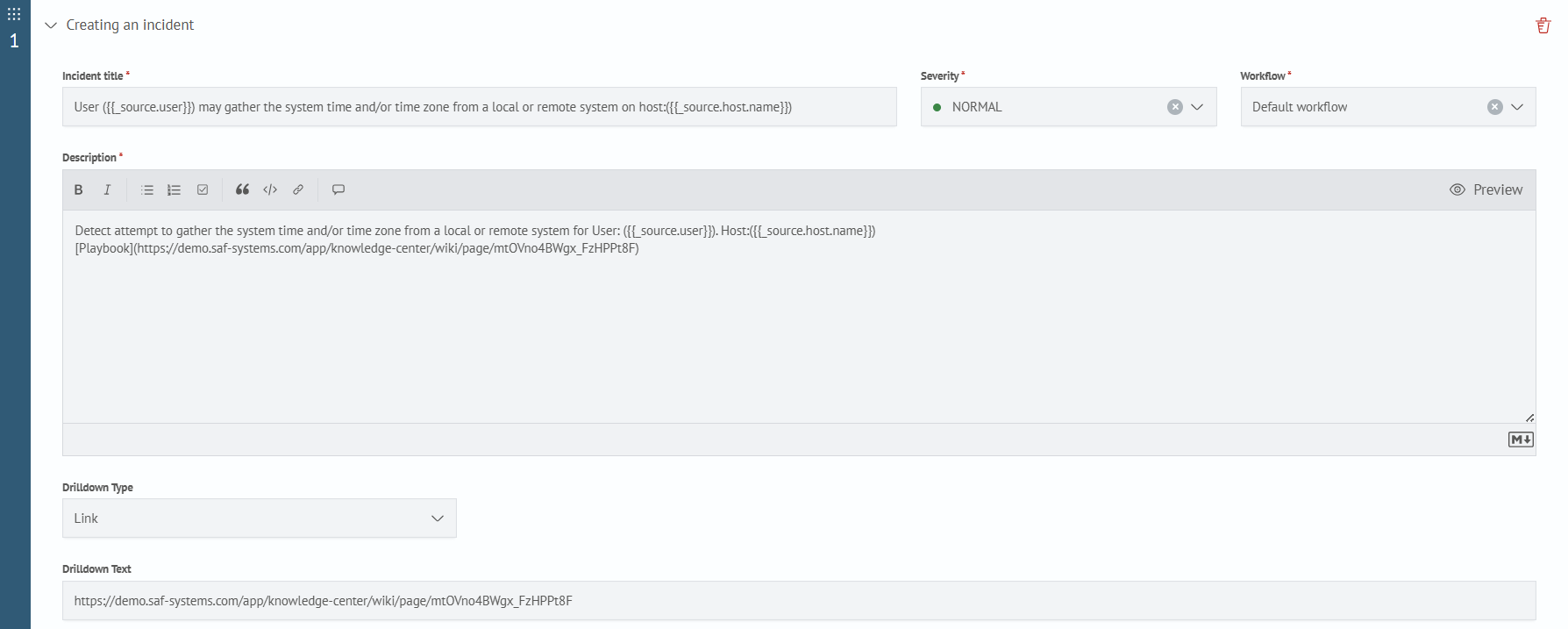
Save this job and wait for it to work. To view the created incident, open Main Menu - Incident Manager - Incident Review.
The screenshot shows that SAF recorded the incident. The incident description contains information about the detected event.