MITRE ATT&CK Module
The module allows applying various MITRE ATT&CK usage scenarios in the protected infrastructure:
- Evaluate the coverage of techniques by tool controls
- Develop specialized threat models and apply them to IT landscape components
- Detect potential technique usage based on event data
Functional Characteristics
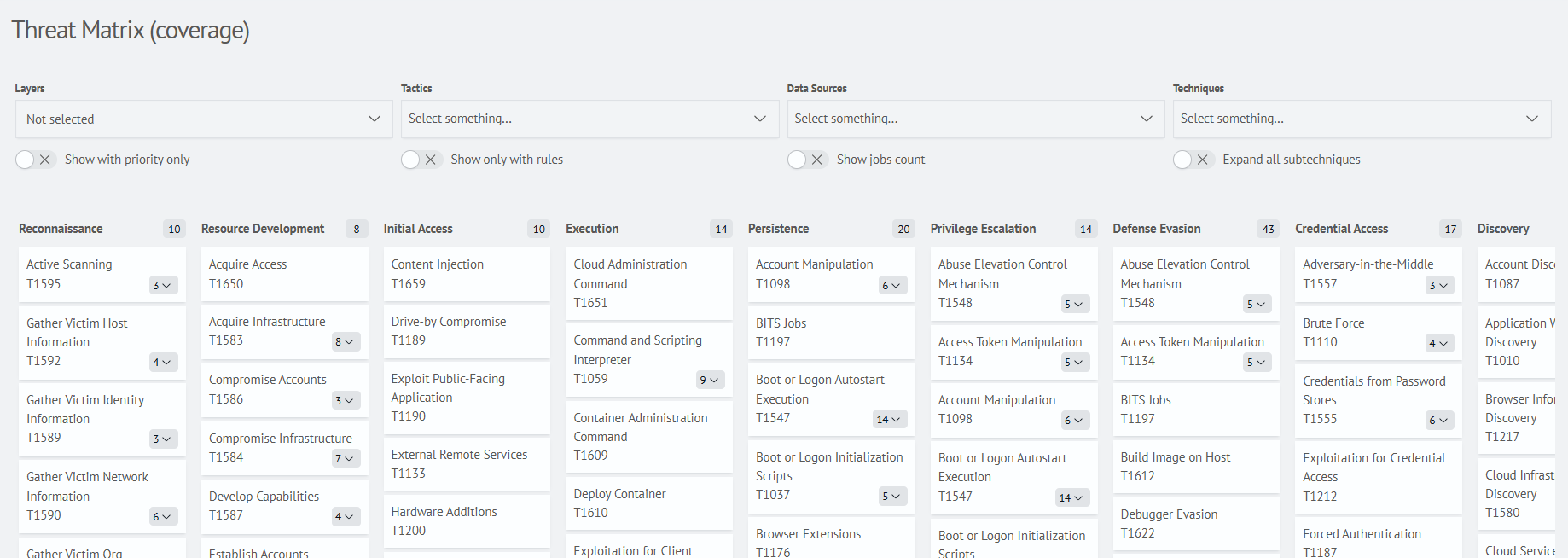
Tactics and Techniques Matrix
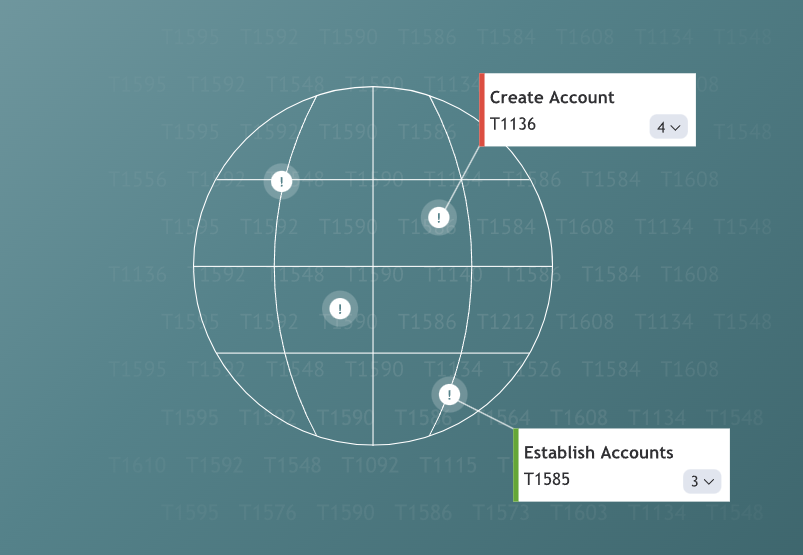
Using a visual interface in the form of a tactics and techniques matrix, it is possible to create threat models by selecting relevant techniques for a specific perimeter/layer.
A set of filters allows quickly selecting only relevant techniques based on the available event sources, platforms. Specific adversary groups can be chosen to focus on techniques used by a particular group (or groups).
Set of Correlation Rules
The module contains a basic set of correlation rules. There is a built-in editor for creating/editing rules.
Each rule is related to a specific technique, tactic, event source. This allows enriching the detection with additional metadata and linking a potential incident, the adversary's goal, and mitigation/remediation recommendations from the MITRE ATT&CK knowledge base.
Incident Detection
For rules that clearly indicate malicious actions in the infrastructure, it is possible to configure incident logging in the Incident Manager module.
Users are provided with a visual interface with a system of filters for analyzing detected techniques with breakdowns by tactics.